Leveraging Continuous View to Hunt Malware. Why hunt for malware? Scanned services Unauthorized systems Patches Config Unauthorized software Malware Malware. - ppt download

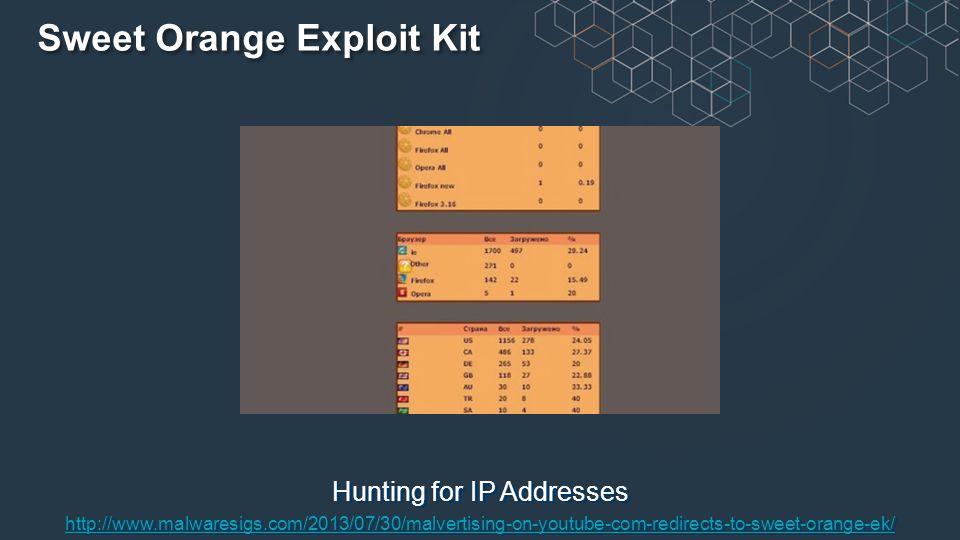
Sweet Orange Exploitation Kit Infection — Malware Traffic Analysis | by Hacktivities | System Weakness